Google's efforts to mark non-secure websites is paying off
Online security is at the forefront of public conscious, and rightfully so. Given the sheer number of people that now use the Internet and the treasure trove of personal data that’s ripe for the picking, it’s no surprise that we’re seeing hacks of epic proportions on a near daily basis.
Fortunately, some of the world’s brightest minds are leading the fight to make the Internet a safer place.
Google in January updated its Chrome web browser to highlight websites that are not encrypted with HTTPS, labeling them as “non-secure.” The idea was two-fold: to help users realize when the site they are visiting is not secure and to motivate site owners to improve security.
The search giant eased into the tactic by first only marking non-encrypted pages that collect passwords or contain credit card form fields. The second phase involved added the warning when people enter data on an HTTP page and on all HTTP pages visited in Incognito mode.
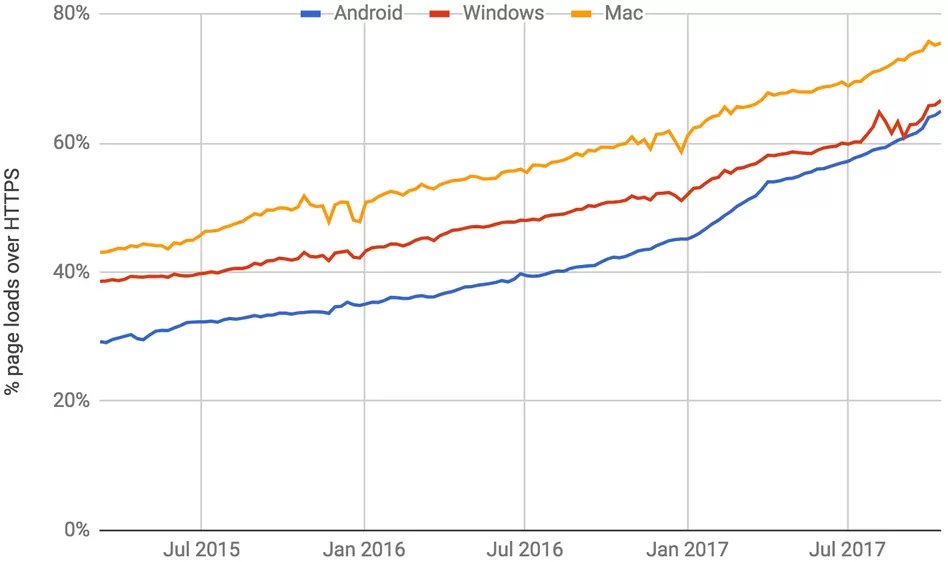
As part of its Cybersecurity Awareness Month, Google on Friday revealed that HTTPS usage over the course of 2017 has made serious progress.
Chrome Security Product Manager Emily Schechter notes that 64 percent of Chrome traffic on Android is now protected, up from just 42 percent a year ago. Furthermore, over 75 percent of Chrome traffic on ChromeOS and Mac is now protected versus 67 percent and 60 percent, respectively, a year ago.
Even more impressive is the fact that 71 of the top 100 sites on the web now use HTTPS. A year ago, only 37 of them could say that.
Changes are happening abroad as well. In Japan, for example, HTTPS usage (measured via Chrome in Windows) has surged from 31 percent to 55 percent over the last year. In Brazil, usage has climbed from 50 to 66 percent.
Encryption is just one of many areas of security that Google is addressing. Earlier this week, the company rolled out a new Advanced Protection feature primarily for those with high-value online accounts. The Chrome team is also reportedly considering taking action against stealth in-browser apps that use the CPU cycles of unsuspecting visitors to mine for cryptocurrencies.













No comments: